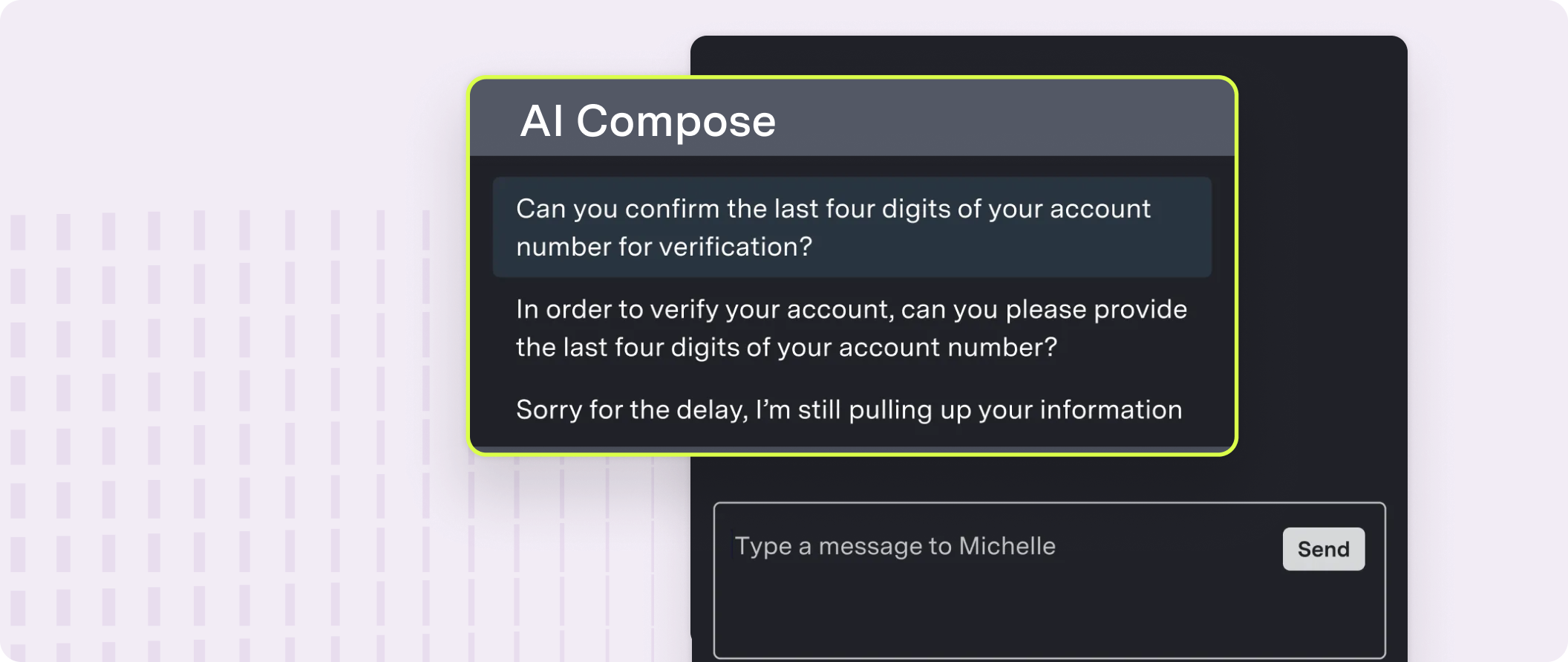
Features
AI Compose provides the following features:| Feature | Description |
|---|---|
| Autosuggest | Provides up to three suggestions that appear in a suggestion drawer above the typing field before the agent begins typing |
| Autocomplete | Provides up to three suggestions that appear in a suggestion drawer above the typing field after the agent begins typing |
| Phrase autocomplete | Provides in-line phrase suggestions that appear while an agent is typing |
| Response quicksearch | Allows in-line search of global and custom responses |
| Fluency correction | Applies automatic grammar corrections that an agent can undo |
| Profanity blocking | Prevents an agent from sending a message containing profanity to the customer |
| Custom response list | Enables management of an individual agent’s custom responses in a simple library interface |
| Global response list | Enables management of global responses in a simple tooling interface |
How it works
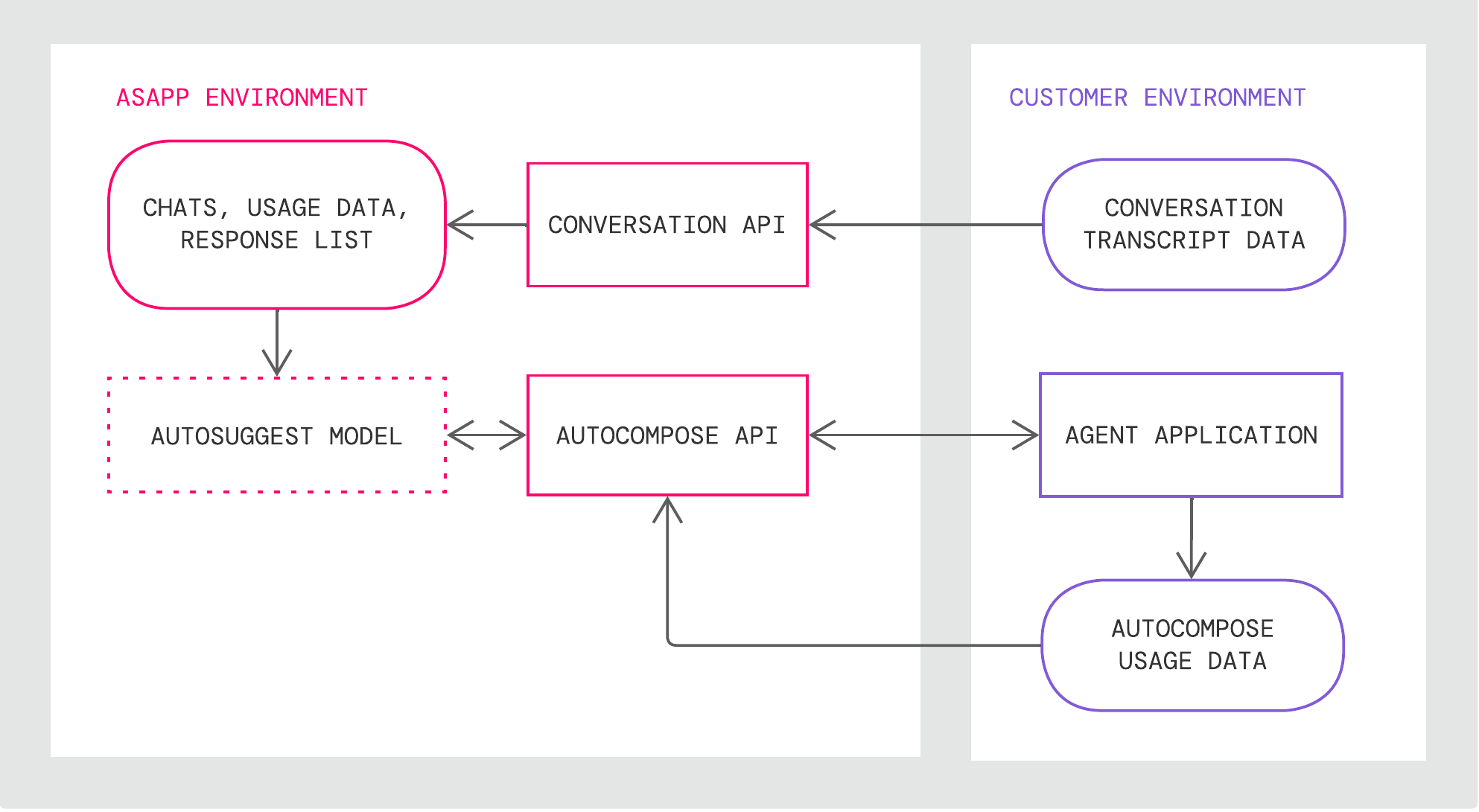
AI Compose takes in a live feed of your agent’s conversations, and then using our various AI models, returns a list of changes or suggested responses based on the state of conversation and currently typed message.- Provide Conversation data via Conversation API.
- In your Agent Application, call the AI Compose APIs to retrieve the list of changes or suggested responses.
- Show the potential changes or responses to your Agent for them to incorporate.
| Component | Description |
|---|---|
| Autosuggest model | LLM Retrained by ASAPP with agent usage data |
| Data Storage | A storage for historical conversations, global response lists and agent historical feature usage that are used for weekly retraining |
| Conversation API* | An API for creating and updating conversations and conversation data |
Get Started
Integrate AI Compose into your applications and upscale your agent response rates.Integrate AI Compose
AI Compose is available both as an integration into leading messaging applications and as an API for custom-built messaging interfaces. For technical instructions on how to implement the service for each approach, refer to the deployment guides below:AI Compose API
Learn more on the use of AI Compose API
AI Compose for LivePerson
Deploy AI Compose via LivePerson
AI Compose for Salesforce
Deploy AI Compose on your Salesforce solution
Use AI Compose
For a functional breakdown and walkthrough of effective use cases and configurations, refer to the guides below:AI Compose Product Guide
Learn more on the use of AI Compose
AI Compose Tooling Guide
Check the tooling options for AI Compose
Feature Releases
AI Compose Feature Releases
Visit the feature releases for new additions to AI Compose functionality
Product and Deployment Guides will be updated as new features become available in production.
Enhance AI Compose
